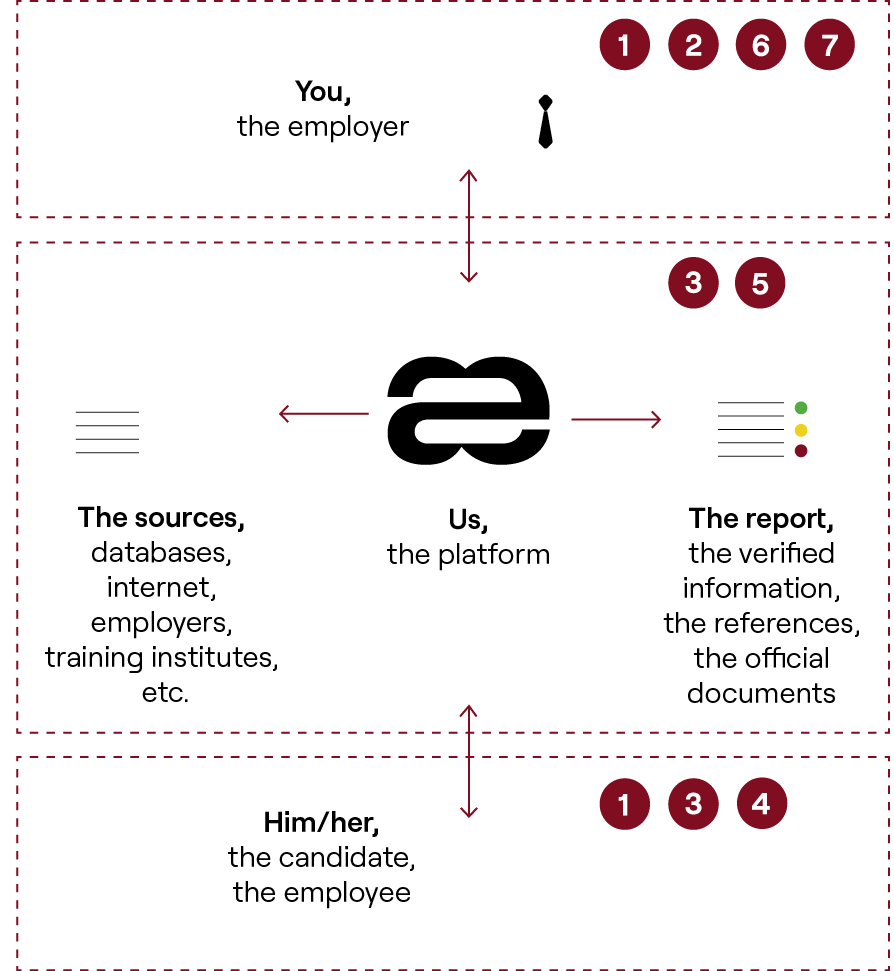
The 7 steps
You inform your candidate that a background check is part of your recruitment process.
You select and order a screening programme on the platform.
Aequivalent contacts the candidate, as your specialised partner, to assist him/her during the process.
The candidate signs the Declaration of Authorisation and confirms his/her information on the platform.
Aequivalent verifies the candidate’s information directly with sources.
You can follow the process, consult the report online and evaluate the results. You can make the results transparent for the candidate.
You have 90 days to download the finalised dossier, before it is deleted.
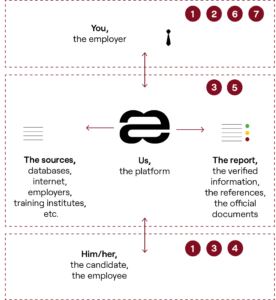
The 7 steps
You inform your candidate that a background check is part of your recruitment process.
You select and order a screening programme on the platform.
Aequivalent contacts the candidate, as your specialised partner, to assist him/her during the process.
The candidate signs the Declaration of Authorisation and confirms his/her information on the platform.
Aequivalent verifies the candidate’s information directly with sources.
You can follow the process, consult the report online and evaluate the results. You can make the results transparent for the candidate.
You have 90 days to download the finalised dossier, before it is deleted.
Information Security
Information Security Responsibilities

Data Protection Officer reachable
at dpo@aequivalent.chSecurity committee advised by security experts
Relations with specialised working groups and authorities
Security Human Resources

Screening of internal and external staff
Regular training and awareness sessions
Individual assessments on Information Security
Access control

Strong password policy with limited validity
Two-step access verification
Network segmentation
Systematic review of accesses and logs
Data Security

Data transport via secure https protocol
Hashed passwords
Daily back-ups
Pentests at regular intervals
Deletion of data 90 days after completion of screenings
Data storage in Switzerland
Operation Security

Application of “Privacy by design & by default” principles
Operational excellence verified by Quality Assurance team
Business continuity planning
Compliance with applicable laws & regulations

Compliance with applicable laws and regulations including the Swiss data protection law and GDPR
Explicit agreement of the applicants, expressed in the Declaration of Authorisation in order to collect information from the competent authorities and reference persons
Transparency of verification programmes
Management of information security incidents

Roles and responsibilities clearly defined
Incident Response Team
Incident reporting and alert procedures
Implementation of a continuity plan, regularly tested
Commitment & Obligation of continuous improvement

Management Priority, see below: “Management quote”
ISO/IEC 27001
Internal and external audits at regular intervals
Information Security
Information Security Responsibilities

Data Protection Officer reachable
at dpo@aequivalent.chSecurity committee advised by security experts
Relations with specialised working groups and authorities
Security Human Resources

Screening of internal and external staff
Regular training and awareness sessions
Individual assessments on Information Security
Access control

Strong password policy with limited validity
Two-step access verification
Network segmentation
Systematic review of accesses and logs
Data Security

Data transport via secure https protocol
Hashed passwords
Daily back-ups
Pentests at regular intervals
Deletion of data 90 days after completion of screenings
Data storage in Switzerland
Operation Security

Application of “Privacy by design & by default” principles
Operational excellence verified by Quality Assurance team
Business continuity planning
Compliance with applicable laws & regulations

Compliance with applicable laws and regulations including the Swiss data protection law and GDPR
Explicit agreement of the applicants, expressed in the Declaration of Authorisation in order to collect information from the competent authorities and reference persons
Transparency of verification programmes
Management of information security incidents

Roles and responsibilities clearly defined
Incident Response Team
Incident reporting and alert procedures
Implementation of a continuity plan, regularly tested
Commitment & Obligation of continuous improvement

Management Priority, see below: “Management quote”
ISO/IEC 27001
Internal and external audits at regular intervals
Management quote
« Due to the nature of our business, data protection is Aequivalent’s core business. Our commitment is reflected through the ISO/IEC 27001 certification process, the international reference for information security management system. »
— Michael Platen, Founder & CEO
Management quote
« Due to the nature of our business, data protection is Aequivalent’s core business.
Our commitment is reflected through the ISO/IEC 27001:2013 certification process, the international reference for information security management system. »
— Michael Platen, Founder & CEO
Frequently Asked Questions
Frequently Asked Questions
Pre-employment verifications
This verification programme allows your (future) employer or client, hereafter “Employer”, to verify important points in your candidate file in order to comply with its internal recruitment or security regulations, and to ensure that you are the person it is looking for for the role it has defined in its organisation.
Depending on your position in the organisation, your employer has defined a number of items to be checked and/or documents to be updated. In your personalised and secure web interface, the access to which is sent by Aequivalent, you will have a complete and exhaustive view of the points that will be checked.
Aequivalent is a specialised company that has been mandated by your Employer to carry out the necessary checks and to draw up an independent and objective report, as well as to help you follow this standardised process. If discrepancies are found, Aequivalent will publish them in its report and your Employer can ask you additional questions. Aequivalent is mandated to carry out checks but only your Employer will decide what actions will be taken, based on the report.
An Employer has rights, obligations and a legitimate interest in collecting information about its future employees and agents, as long as it only collects information that is relevant to ensuring their ability to perform a given role. Therefore, your consent is not legally required for information to be collected about you.
Although your Employer has the right to collect certain information about you, Aequivalent requires you to sign the Authorisation Statement before beginning the verification process. This document ensures that you have been informed by your Employer beforehand that it has mandated Aequivalent to collect and verify your information. The signature of the Authorisation Statement is also necessary to obtain information from third parties according to the verifications that your Employer has ordered from Aequivalent (competent authorities, such as the office responsible for obtaining an extract from your criminal record, prosecution office, universities, references, …) and to establish a personality profile.
Yes, your Employer has put in place a background check policy and uses the services of Aequivalent to ensure that the process is carried out according to best practices. However, if you do not want your information collected, you have the right to refuse. If you are considering refusing to participate in the verification programme, we advise you to discuss this with your Employer beforehand, who will decide how to respond to your refusal.
Your data is processed by Aequivalent on behalf of your Employer, who decides on the processing. Therefore, any questions regarding the results of the checks should be addressed to your Employer. Aequivalent is ISO/IEC 27001:2022 certified and uses your data and documents only for this specific and unique verification programme. Aequivalent automatically deletes all data and documents concerning you 90 days after the report to your employer. In addition, you can request a faster deletion of your data at any time via your personalised access to the platform.
In-employment verifications
This verification programme allows your employer to update your personnel file in order to comply with its internal human resources or security regulations.
Depending on your position in the organisation, your employer has defined a number of items to be checked and/or documents to be updated. In your personalised and secure web interface, the access to which is sent by Aequivalent, you will have a complete and exhaustive view of the points that will be checked.
Aequivalent is a specialised company that has been commissioned by your employer to carry out the necessary checks and to draw up an independent and objective report, as well as to help you follow this standardised process. If discrepancies are found, Aequivalent will include them in its report and your employer can ask you additional questions. Aequivalent is mandated to carry out checks, but it is your employer who will decide what actions to take, based on the report.
An employer has rights, obligations and a legitimate interest in collecting information about its employees, as long as it only collects information that is relevant to ensuring their ability to perform a given role. Therefore, your consent is not legally required for information to be collected about you.
Although your employer has the right to collect certain information about you, Aequivalent asks you to sign the Authorisation Statement before starting the verification process. This document ensures that you have been informed by your employer beforehand that he or she has mandated Aequivalent to collect and verify your information. The signature of the Authorisation Statement is also necessary to obtain information from third parties according to the verifications that your employer has ordered from Aequivalent (competent authorities, such as the office responsible for obtaining an extract from your criminal record, prosecution office, etc.) and to establish a personality profile.
Yes, your employer has put in place a verification policy and uses Aequivalent’s services to ensure that the process is carried out according to best practices. However, if you do not want your information to be collected, you have the right to refuse. If you are considering refusing to participate in the verification programme, we advise you to discuss this with your employer beforehand, who alone will decide what action to take.
Your data are processed by Aequivalent on behalf of your employer, who decides on the processing. Therefore, any questions regarding the results of the checks should be addressed to your employer. Aequivalent is ISO/IEC 27001:2022 certified and uses your data and documents only in the context of this specific and unique verification programme. Aequivalent automatically deletes all your data and documents 90 days after the report to your employer. In addition, you can request a faster deletion of your data at any time via your personal access to the platform.